Identity-First AI Agent Security
AI agents are quickly becoming first‑class actors in the enterprise, writing code, accessing data, calling APIs, and making decisions at machine speed. Token Security is the AI Agent Security Platform built to give organizations complete confidence in how AI agents are created, governed, and operated without slowing innovation.
Our platform is built on three foundational pillars
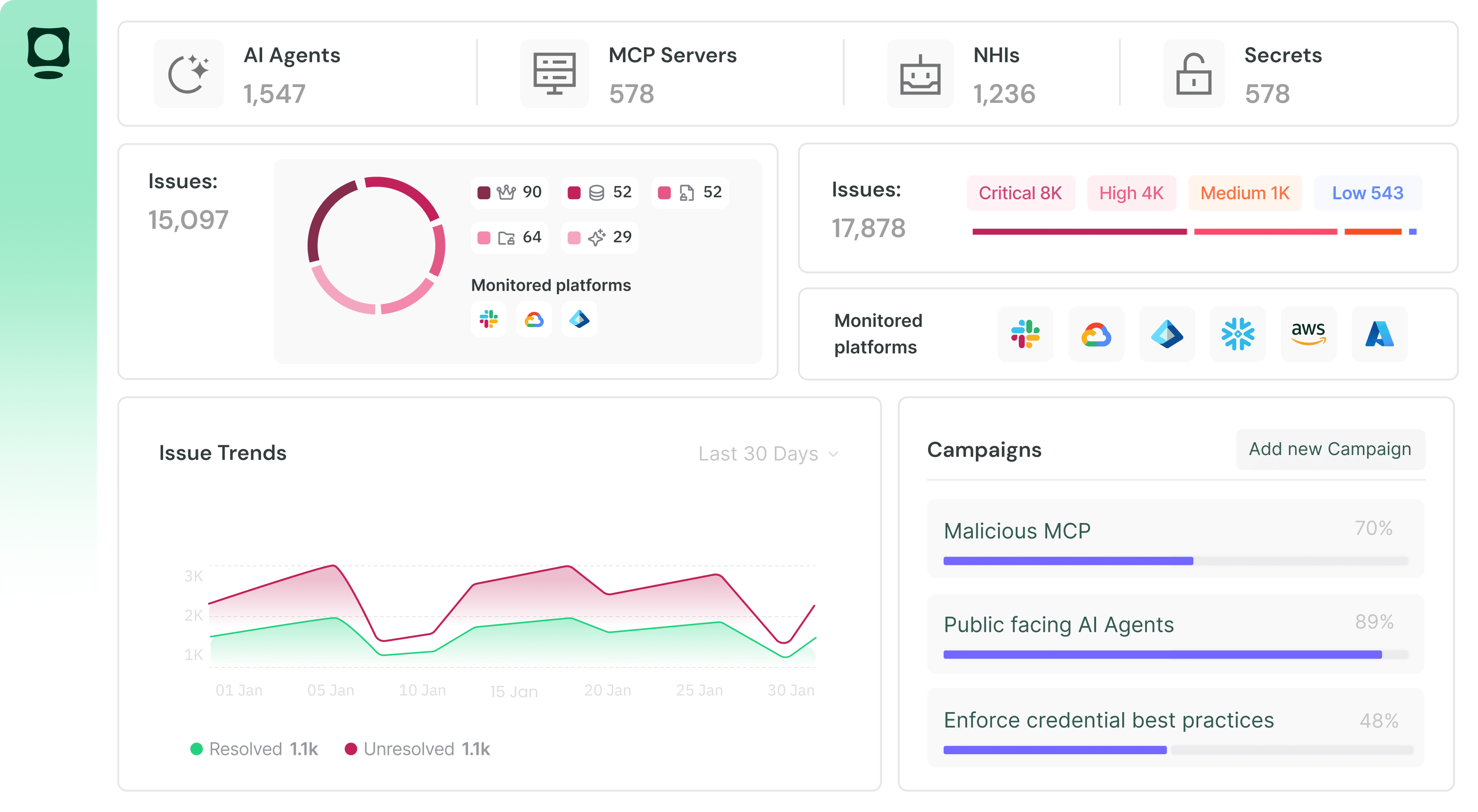
Know Every AI Agent, Everywhere
You can’t secure what you can’t see. Token Security provides deep, continuous visibility into AI agents across cloud environments, SaaS platforms, internal tools, and custom frameworks.
Discover and Inventory AI Agents
Token Security automatically discovers AI agents and MCP servers. This includes:
- Autonomous agents and copilots
- Service‑integrated agents and bots
- Agent frameworks and orchestration layers
- The non‑human identities and tokens they use
.png)
Understand Behavior and Access
Go beyond static inventories. Token Security maps how agents actually operate.
- Who owns the agents
- Which APIs, services, and systems they have access to
- What permissions and credentials they rely on
- How they behave over time
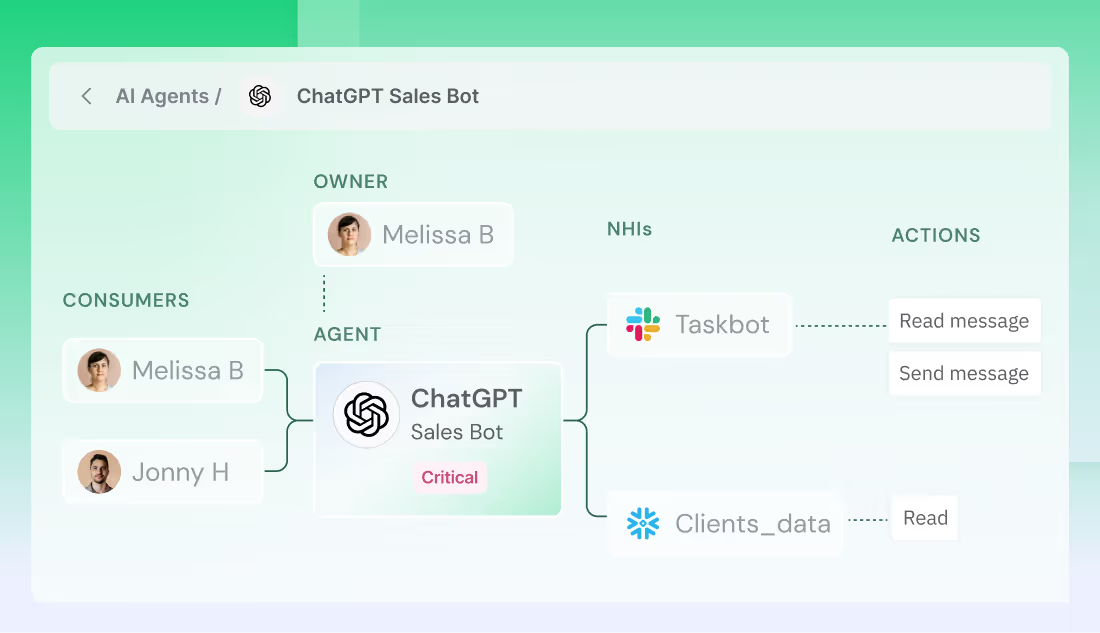
Enforce Least Privilege for AI Agents
AI agents move fast and so do their risks. Token Security gives you precise, automated control over what agents can access and do.
Intent-Based Permissioning for AI Agents
Token Security enables intent-based permissioning to align access with what an AI agent is meant to do, not just what credentials it holds.
- Define permissions based on agent purpose and expected actions
- Replace long-lived, over-scoped credentials with purpose-bound access
- Automatically enforce least privilege as agent behavior and intent evolve
- Eliminate risky authentication patterns that grant agents unnecessary power
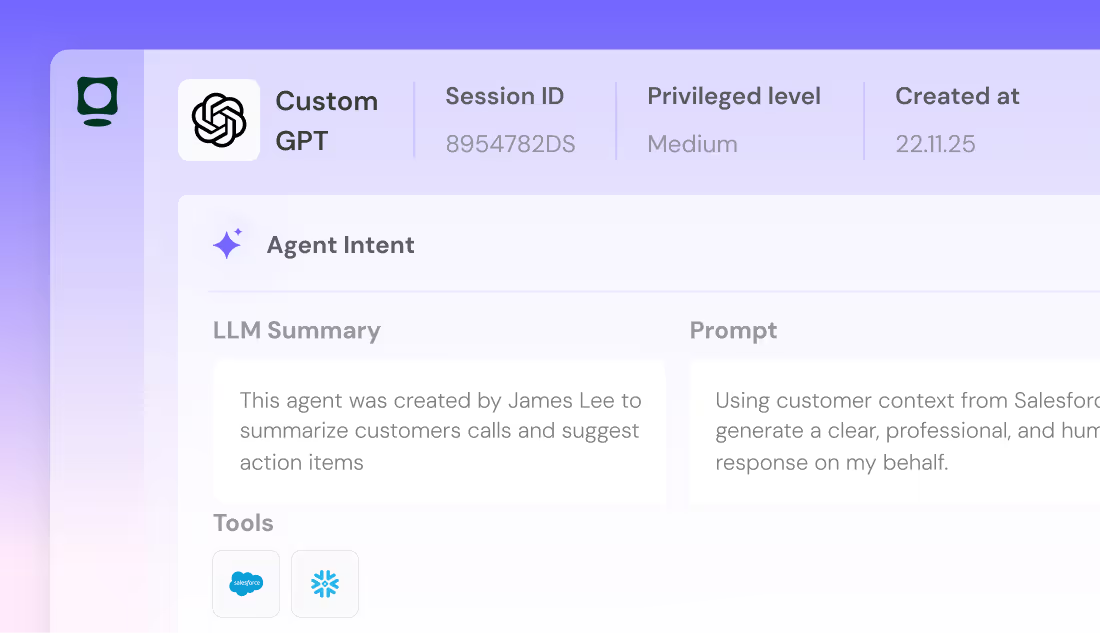
Right‑Size Permissions Automatically
Token Security identifies excessive, unused, or risky permissions granted to AI agents and the non‑human identities behind them.
- Remove standing privileges
- Enforce least privilege access
- Reduce over‑permissioned tokens and service accounts
- Automatically right-size permissions based on contextual awareness
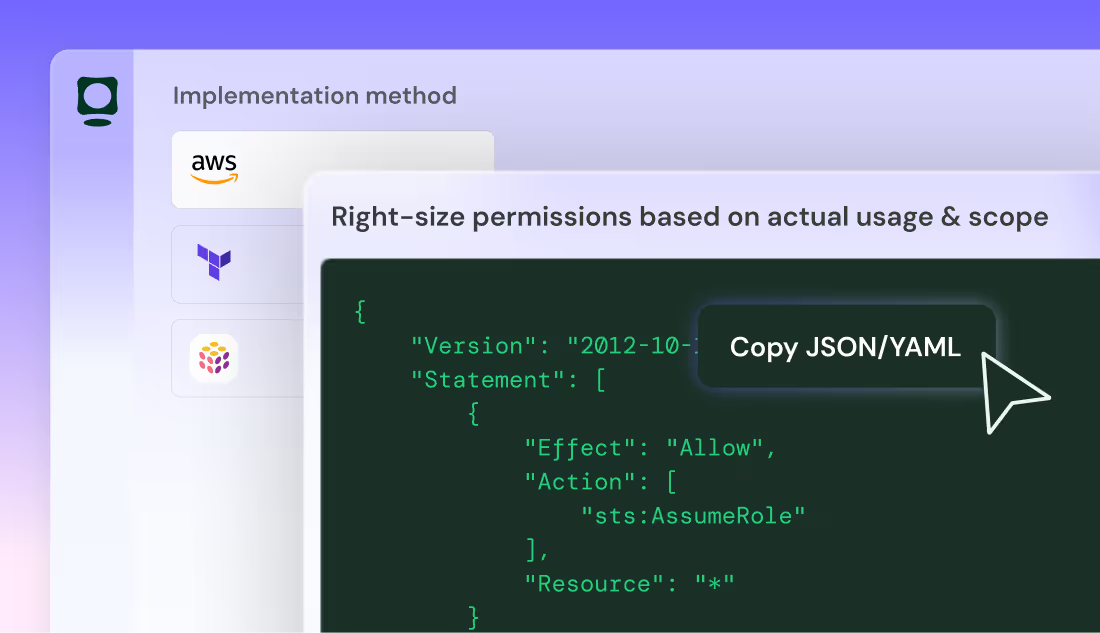
Set the Rules for AI Agent Trust
As AI agents become core to business operations, security must move from ad‑hoc controls to formal governance.
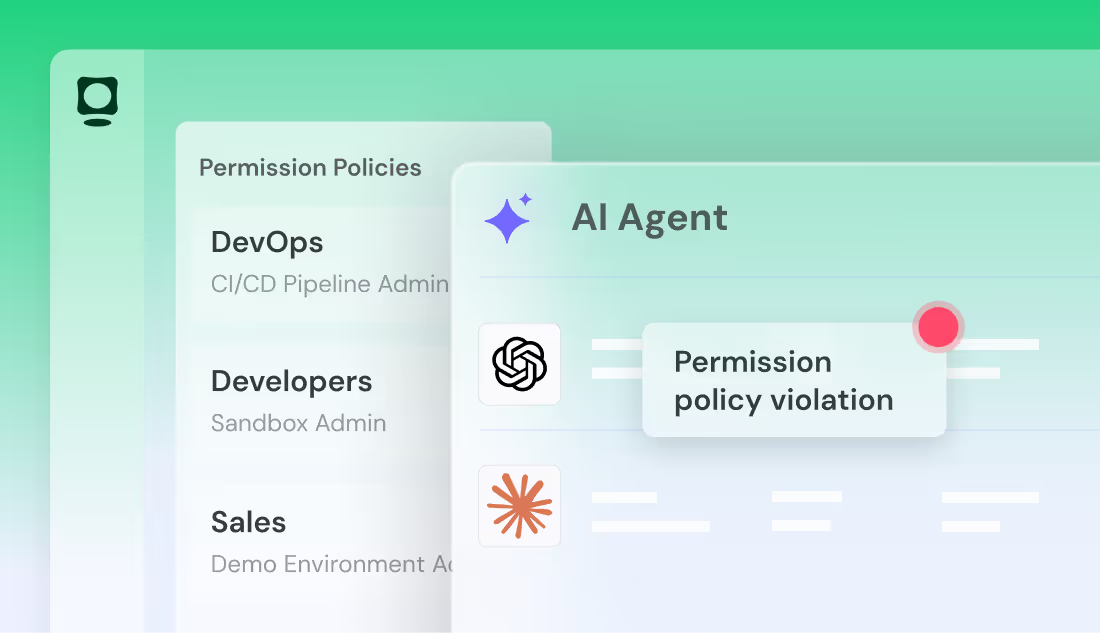
Define Agent Security Policies
Token Security allows organizations to define clear policies for AI agent creation, access, and operation, including:
- Approved services and data sources
- Allowed tools and integrations
- Credential usage requirements
- Environmental and runtime constraints
Establish Continuous Compliance and Auditability
Token Security continuously evaluates agents against internal policies and external requirements, providing:
- Ongoing compliance validation
- Clear audit trails of agent actions
- Evidence and forensics for security and risk reviews
One Platform for the AI Agent Era
Token Security unifies Visibility, Control, and Governance into a single platform purpose‑built for AI agents and non‑human identities.

Designed for autonomous systems

Built for modern cloud and AI stacks

.gif)



