The Machine Identity Attack Surface - MITRE ATT&CK FRAMEWORK Redefined
.avif)
The shift to cloud computing, the proliferation of mobile devices, the rise of remote work, and the surge in enterprise software applications have widened the attack surface for hackers to breach organizations. The expanded attack surface and additional access points allow cybercriminals to be increasingly inventive in their methods. As a result, companies are experiencing more severe financial losses and reputational harm due to security breaches. According to a report published in 2024 by ITRC (Identity Threat Resource Center), the number of reported compromises increased from 1,801 data compromises in 2022 to 3,205 in 2023, that is a 78% increase over the year.
This blog reviews some of the most devastating security breaches that happened recently, focusing on the impact of vulnerable non-human identities on attack progression. By examining how these vulnerable identities affect the MITRE ATT&CK framework, it is clear that attackers can escalate attacks quickly, leading to a significant reduction in the response time window. Non-human identities, such as service accounts, tokens and access keys, play a crucial role in these breaches, illustrating the importance of securing these areas to prevent attack escalation.
Navigating the Complexity of Machine Identity Management
Machine identities are employed by entities that cannot change passwords or support multi-factor authentication. Typically, these identities use long, non-expiring passwords. To enhance security, many organizations implement policies to regularly rotate or change these passwords. However, if the machine identity is embedded in an application or used by a tool, changing the password can break the application's or tool's functionality due to dependency on the specific identity.
Public cloud vendors manage identities in a proprietary IAM service, such as AWS IAM service or Azure Managed Identity service. In on-premises settings, organizations can address this challenge through privileged access management tools like Thycotic or CyberArk, which can identify machine identities and their dependencies. Organizations transitioning to the cloud find it challenging to create a clear and coherent map of identities and their related dependencies. Traditional solutions, designed for on-premises environments, often fall short in addressing the unique complexities of cloud-based systems.
Discovering machine identities and creating an accurate inventory of them is a crucial first step in securing these assets. This encompasses service accounts, managed identities, and APIs, among other identity-based resources.
Recent Attacks
Three major security breaches over the last year highlight the impact of mismanaged non-human identities and show how the attack surface has evolved and impact the response time window. The unique characteristics of non-human identities require new approaches to address their vulnerabilities and reduce the risks associated with a broader attack surface and shorter response times.
Sisense Data Breach
According to a report from the US CISA (Cybersecurity and Infrastructure Security Agency), attackers breached a company's self hosted GitLab code repository, where they found a token or credential that allowed them to access Sisense's Amazon S3 cloud storage. From there, they copied and exfiltrated several terabytes of Sisense customer data, including millions of access tokens, email account passwords, and even SSL certificates. As a result, the attackers now possess the credentials used by Sisense customers in their dashboards. It remained unclear if these credentials were exploited by malicious actors. Consequently, the US CISA has directed Sisense customers to reset their account login credentials, secrets and tokens and report any suspicious activity involving the use of compromised credentials.

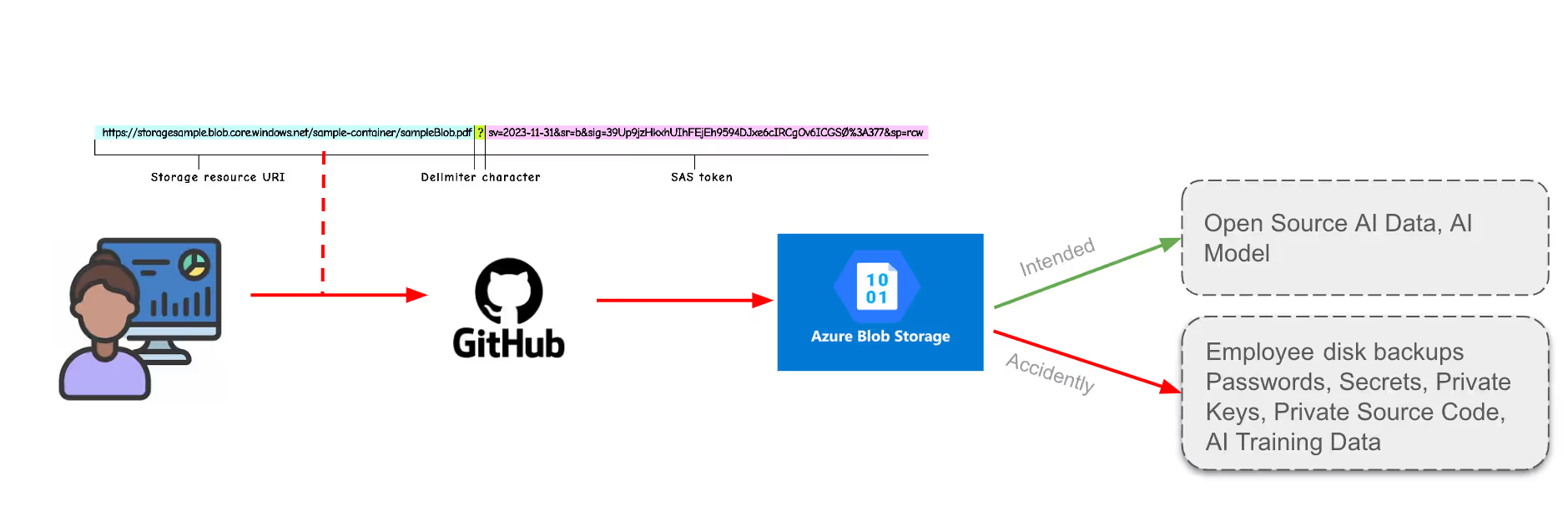
Microsoft - 38TB of Data Accidentally Exposed by Microsoft AI Researchers
Microsoft's AI research team accidentally exposed 38 terabytes of private data when they published open-source training data on GitHub. Although they intended to share specific open-source AI data, the exposure included a disk backup from two employees' workstations, which contained sensitive information such as secrets, private keys, passwords, and over 30,000 internal Microsoft Teams messages.
The researchers used Azure's SAS (Shared Access Signature) tokens to share files, which normally allows for restricted file sharing. However, the link was mistakenly set to share the entire storage account, unintentionally exposing 38TB of additional private files.
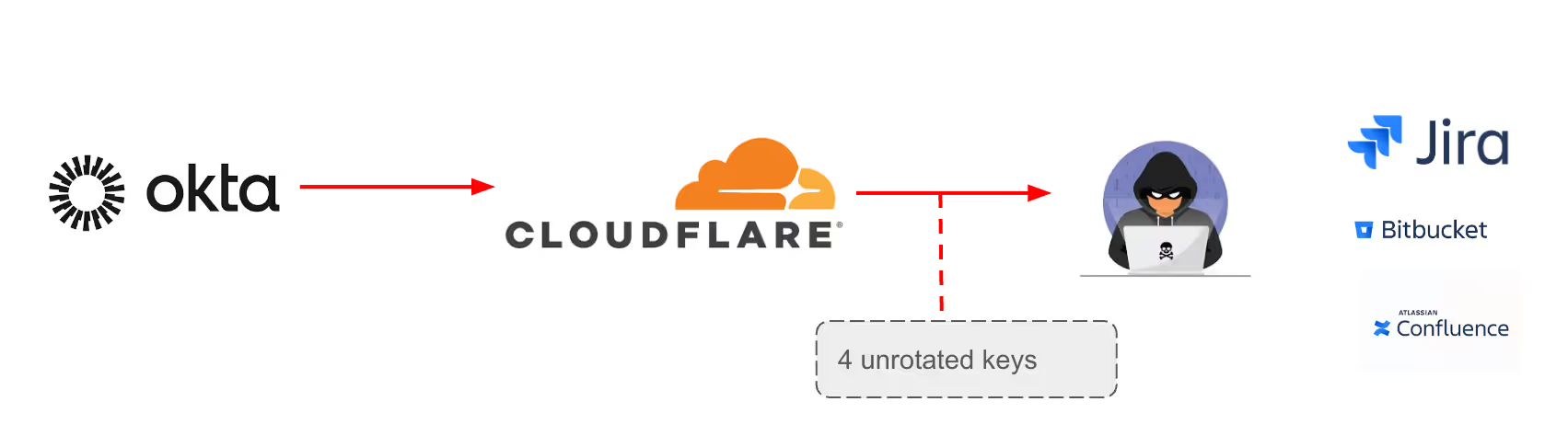
Cloudflare Data Breach
Initially, attackers breached Okta’s support ticketing system using a compromised service account, resulted in stolen customer’s artifacts that contained credentials. Cloudflare, a customer of Okta, reacted to the initial breach by rotating 5,000 exposed credentials, aiming to minimize the impact of the attack. Unfortunately, their efforts were not entirely successful. According to an in-depth report released by Cloudflare after the attack in 2023, Cloudflare revealed that, a few weeks after the incident, Okta attackers leveraged two credentials that weren't rotated to infiltrate Cloudflare's Atlassian suite. These credentials—a token and service account details, both related to integrations within Cloudflare’s Atlassian environment—were used to gain administrative access to Cloudflare's Jira, Confluence, and Bitbucket. This oversight allowed attackers to penetrate Cloudflare's internal systems despite their initial efforts to mitigate the breach.
Challenges and Risks in Managing Machine Identities
Machine identities present significant challenges for organizations because of their unique characteristics. Among many other factors, these are the key reasons why managing machine identities is challenging and can increase their vulnerability:
- Lack of MFA - Multifactor authentication (MFA) is increasingly seen as an essential component of a robust identity and access management (IAM) policy for all human users. However, this security measure is typically not applicable to non-human accounts, as these are not linked to individual employees. This absence means there's no secondary verification to prevent breaches if these credentials are compromised.
- Permissive Access - Accounts used either for integration purposes or provisioned for applicative purposes are typically established as service accounts with elevated administrative privileges. In many instances, this privileged access reaches deep into the core technology stack of the enterprise. As a result, these non-human accounts can be particularly risky if compromised, as they can perform a wide range of actions, including read, write, and delete. Unlike human accounts, which undergo regular permission reviews, non-human accounts rarely have their permissions audited or revoked, heightening the risk in the event of a breach.
- Always Active - Non-human identities, such as API keys and tokens, operate at a steady pace, which makes it harder to detect subtle malicious activities. In contrast, human accounts that show sudden activity spikes, especially during off-hours or holidays, are more likely to trigger alerts due to their unusual behavior. Data breaches that go undetected for extended periods often involve non-human identities, as their constant activity can conceal signs of abnormal behavior.
MITRE Attack Framework for non-human Identities
The MITRE ATT&CK framework provides a comprehensive approach to understanding how traditional attack scenarios unfold in cloud environments, typically exploiting user credentials within Infrastructure as a Service (IaaS). Here's a typical sequence of attack tactics and techniques using the MITRE framework for IaaS environments:
- Initial Access - attackers gain entry through various methods, such as phishing or exploiting cloud service vulnerabilities.
- Execution - attackers execute malicious code to further their goals.
- Persistence - attackers establish mechanisms to maintain access over time.
- Privilege Escalation - attackers increase their level of access within the cloud environment.
- Defense Evasion - attackers employ tactics to avoid detection by security systems.
- Credential Access - attackers seek to obtain sensitive credentials for further access.
- Discovery - attackers explore the environment to understand its structure and identify targets.
- Lateral Movement - attackers move across different cloud services or instances.
- Collection - attackers gather sensitive information from the cloud environment.
- Exfiltration - attackers remove data from the cloud environment.
- Impact - attackers cause harm to disrupt operations or destroy data.
Typical Attack Scenario:
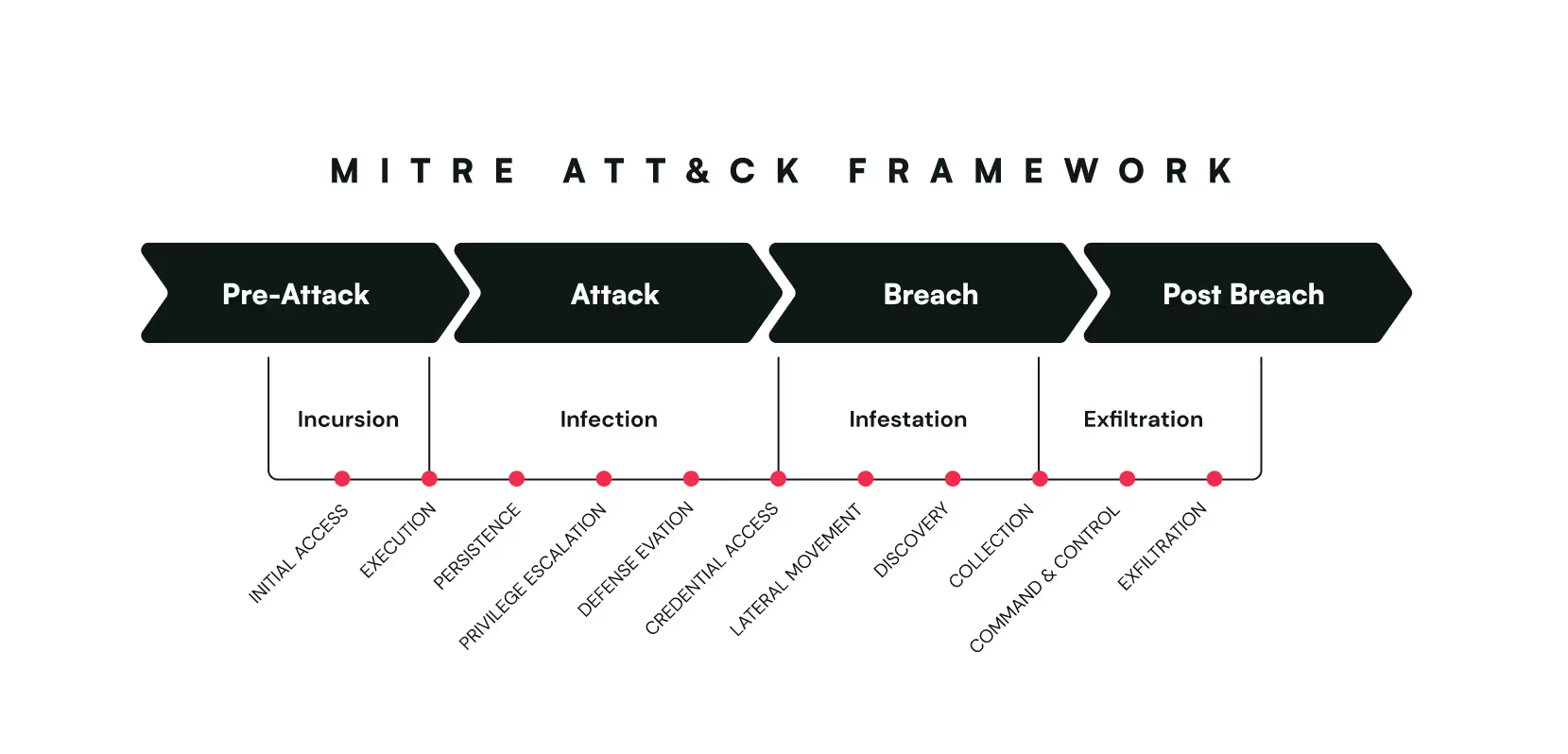
When attackers exploit non-human identities, such as API keys or service accounts, they often bypass the initial steps of an attack—such as gaining initial access, executing malicious code, establishing persistence, escalating privileges, and evading defenses. These non-human identities typically already possess the necessary permissions and access required for further malicious activities. Therefore, attackers can directly jump to step 6, which involves accessing and manipulating credentials. This allows them to immediately start exploring the environment, moving laterally, and accessing sensitive data without needing to compromise human accounts or overcome additional security measures.
Typical attack Scenario involving non-human identity:
.avif)
Token’s Machine First Approach
As a veteran of Cloud Detection and Response based solutions and one of the primary inventors of this domain, I suggest a unique strategy for safeguarding non-human identities. At Token Security, we offer a comprehensive solution designed to address the complex and evolving nature of cloud identities. Our approach encompasses several critical aspects:
- Inventory Management: Establish a thorough inventory of non-human identities (NHIs), creating a detailed map of all the service accounts, tokens, and API keys in your environment.
- Risk-Based Prioritization: Prioritize NHIs based on their potential impact and likelihood of being compromised, allowing you to focus your security efforts on the most critical identities.
- Automated Protection: Implement automated mechanisms to identify vulnerable NHIs and apply rotation procedures to ensure they remain secure.
- Least Privilege Compliance: Ensure that all NHIs operate with the minimum necessary privileges, reducing the potential attack surface.
- Continuous Monitoring: Monitor NHIs for anomalous activity, alerting you to any suspicious behavior that might indicate an ongoing attack.
By addressing these aspects, our solution provides a robust defense against threats targeting non-human identities, allowing your organization to operate securely in a cloud-based environment.
.gif)