The Ultimate Non-Human Identity Security Guide
.avif)
As organizations embrace modern technologies — from cloud-native apps and SaaS platforms to AI-driven systems and containerized infrastructure — a new class of identities is quietly exploding in scale: Non-Human Identities (NHIs). These include service accounts, tokens, roles, and machine credentials used by applications, automation pipelines, and AI agents. Unlike human identities, which are typically centralized and managed through a single identity provider, NHIs are decentralized by nature. They’re spun up dynamically across platforms, provisioned through Infrastructure-as-Code (IaC), and often created by developers, DevOps, cloud engineers, and even autonomous systems. This proliferation makes them hard to track, even harder to govern, and nearly impossible to secure without the right visibility and controls. Security teams are losing sight of what exists, who owns what, and what each identity can access. And when you don’t know an identity exists, you can’t enforce guardrails, detect risk, or respond to compromise.
That’s why we’ve built the Non-Human Identity Security Guide (available at NHIguide.ai) — a dedicated resource to help you navigate the growing NHI landscape, understand the risks, evaluate security solutions with clarity, and make better-informed decisions to protect your infrastructure in 2025 and beyond. Developed in collaboration with a global group of CISOs and security leaders from respected organizations, this guide captures real-world expertise to help teams tackle NHI challenges with confidence and precision.
What’s Inside the Non-Human Identity Security Guide?
This guide was authored by security leaders from Udemy, Klaviyo, Lemonade, Elastic, Dayforce, ZoomInfo and more. It’s designed to help CISOs and security practitioners tackle NHIs head-on — with actionable insights and a vendor-neutral roadmap to success.
Here’s what you’ll learn:
Understand the NHI Fundamentals
- What are NHIs, and how do they differ from human users
- Why NHIs are inherently riskier and more complex to manage
- Real-world case studies of NHI-based breaches
- What should I look for when choosing a Non-Human Identity (NHI) security solution or vendor
Understand NHI Challenges
- Proliferation of Identities
- Lack of Visibility
- Lack of Operational Context
- Overprivileged by Nature
- Lack of Real-Time Monitoring
- Complex Lifecycle Management
- Slow and Ineffective Remediation
- No control on NHIs at runtime
Choosing a security solution for NHIs is tricky. Our guide lays out key evaluation criteria, including:
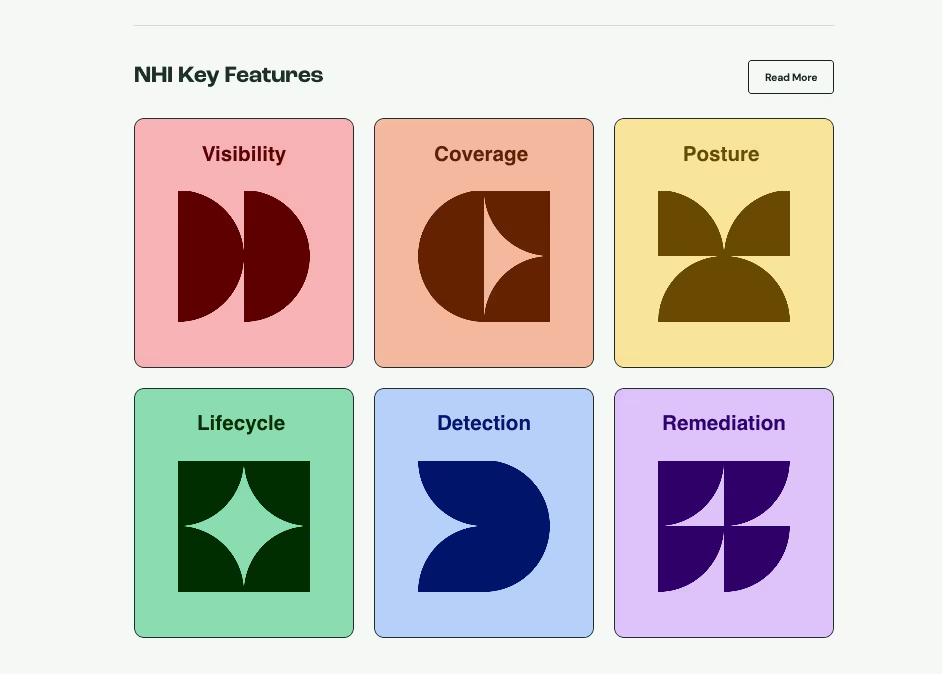
- Coverage – Identifying service accounts, tokens, API keys, SSH keys, IAM roles, and other non-human credentials to establish a clear inventory of NHI usage and ownership.
- Visibility - Ensuring organizations maintain an inventory of NHIs, authentication methods, and entitlements while identifying owners and visualizing the blast radius of any NHI.
- Posture – Enforcing least privilege, eliminating misconfigurations, ensuring alignment with compliance frameworks, and mitigating threats like weak authentication, dormant identities, and over-privileged access.
- Lifecycle – Automating credential provisioning, rotation, and decommissioning to reduce manual effort and security gaps.
- Detection – Identifying active threats and anomalous behavior, enabling teams to remediate risks confidently and intervene when needed.
- Remediation - Accelerate remediation by triggering workflows and automatically routing alerts with prescriptive instructions to the right person.
As shown in the below screenshot each section of the NHI Guide is structured to help security teams deeply understand and evaluate a specific area of Non-Human Identity (NHI) security. At the top, you’ll find a “Vendor Capability” overview, which outlines the purpose of the functionality and explains why it’s important to secure NHIs. Below, we’ve included “Questions to Ask an NHI Provider”, a curated set of practical questions designed to help buyers assess whether a vendor delivers on the capabilities described. These questions directly relate to the “Success Criteria” table, which breaks down each feature into specific requirements and outcomes, making validating vendor claims and identifying gaps easier. This structure ensures buyers can confidently compare solutions and make informed decisions backed by real-world security needs.
https://nhiguide.ai/features/visibilty
A Practical RFP to Guide Your NHI Security Evaluation
A central component of the Non-Human Identity Security Guide is the downloadable Request for Proposal (RFP)
— a practical tool designed to help organizations evaluate NHI security solutions with structure and depth. This RFP breaks down each evaluation criterion into three clear elements:
- List of required functionalities
- Detailed explanation of how to assess them
- Designation of whether each capability is a minimum or advanced requirement.
It was developed in collaboration with CISOs and security leaders from cloud-native, on-premise, and hybrid enterprises, representing various technology stacks, architectures, and maturity levels. Whether you’re a born-in-the-cloud startup or a global enterprise mid-way through cloud migration, this RFP guides you through the nuances of NHI discovery, lifecycle management, security posture, and remediation. The final section focuses on enterprise readiness, helping buyers assess whether a solution can scale to meet real-world needs — including integrations with SIEM, SOAR, collaboration tools, APIs, and reporting systems.
Types of NHI Vendors in the Market
As Non-Human Identity Security gains traction, a diverse range of vendors have emerged, each tackling the challenge from a unique angle. Understanding the different types of solutions can help you align your organization’s needs with the right capabilities. Here are the main categories of NHI security vendors found in the market today:
1. SaaS-Oriented NHI Vendors
These vendors specialize in securing non-human interactions between corporate SaaS applications — particularly SaaS-to-SaaS connectivity. Their focus is on API keys, OAuth applications, and integrations across platforms like Salesforce, HubSpot, Slack, or GitHub. They often cover shadow SaaS detection, identifying unauthorized apps that employees connect to without IT oversight. Capabilities typically include:
- Discovering rogue or unmanaged SaaS apps
- Prioritizing risk based on data access and permissions
- Mapping OAuth connections and third-party app usage
- Identifying and alerting on malicious or misused API keys
This approach is well-suited for organizations with a sprawling SaaS ecosystem and concerns around visibility, third-party integrations, and policy enforcement at the SaaS layer.
2. Secrets Scanning and NHIDR-Focused Vendors
This category centers on secrets discovery and detection of malicious activity across the software development lifecycle. These vendors specialize in identifying secrets (like API keys and tokens) leaked in source code, collaboration platforms (e.g., Slack), file repositories, or misconfigured systems. They often position themselves around Non-Human Identity Detection and Response (NHIDR). Common capabilities include:
- Secrets scanning in code, config files, or other platforms
- Detection of unvaulted or long-lived secrets
- Secrets lifecycle management and automatic rotation
- Alerting on suspicious usage of known secrets
- Enforcement of secrets management best practices
This approach is effective for developer-heavy environments with complex pipelines, where secrets sprawl is a top concern.
3. Vault and Rotation-Centric Vendors
These vendors focus primarily on automating key and secret rotation — often assuming that secrets are already stored in a secure vault. Their strength lies in integrations with secret managers and their ability to rotate credentials on a scheduled or event-based basis. Key features typically include:
- Inventory of vaulted credentials
- Policy-driven rotation workflows
- Expiry enforcement and access auditing
- Support for compliance standards around credential rotation
However, this approach often underestimates the complexity of rotation on the consumer side — especially when secrets are deeply embedded in applications, legacy scripts, or third-party tools without re-deployment pipelines.
4. Context-Driven Vendors
These vendors take a holistic and context-aware approach to NHI security. Rather than focusing on a single attack surface, they prioritize contextual visibility — combining identity posture, runtime activity, and infrastructure ownership data. They often integrate with Infrastructure-as-Code (IaC) to trace identity origins and assign ownership to specific engineers or teams. Their platforms typically offer:
- Rich identity access graphs and usage analytics
- IaC linkage and ownership attribution
- Continuous inventory of NHIs across cloud, SaaS, PaaS, and more
- Posture management and permission drift detection
- Lifecycle controls from provisioning to decommissioning
This category is ideal for organizations seeking broad coverage across hybrid environments — including both cloud-native and migrating infrastructures — and needing full visibility into who created, owns, and uses each identity.
Comparison Table: SaaS Oriented vs. Secrets Scanning vs. Rotation-Centric vs. Context Driven Vendors
How Does Token Security Help You Navigate Through These Risks?
Token Security was purpose-built to address the most pressing challenges of Non-Human Identity (NHI) sprawl, complexity, and risk across modern environments. Our platform provides deep, context-aware protection by combining discovery, posture management, lifecycle automation, and threat response — all tied back to real usage and ownership. Here’s how we help security teams take control:
✅ Comprehensive Discovery: Automatically inventory NHIs across cloud, SaaS, CI/CD, AI agents, and on-prem systems — including shadow identities and unmanaged secrets.
✅ Contextual Visibility: Map each identity to its human owner, IaC source, and usage patterns to build an access graph and understand blast radius.
✅ Posture Management: Continuously assess and surface misconfigurations, over-privileged identities, dormant credentials, and secrets not stored in vaults.
✅ Lifecycle Automation: Enable ownership assignment, key rotation, decommissioning of unused identities, and migration of secrets to vaults — all backed by infrastructure-as-code integration.
✅ Threat Detection: Monitor NHIs in real time for anomalous behaviors, privilege escalation attempts, and risky usage across environments.
✅ Prescriptive Remediation: Route actionable alerts with AI-generated, IaC-aware remediation guidance directly to the responsible teams.
✅ Enterprise Readiness: Integrate seamlessly with SIEM, SOAR, ITSM tools, and reporting systems — ensuring alignment with security, compliance, and operational workflows.
With Token Security, teams gain end-to-end control over NHIs — from visibility to action — enabling scalable, policy-driven identity governance across dynamic and hybrid infrastructures.
Ready to Secure Your NHIs?
Visit NHIguide.ai to explore the framework, download the full NHI RFP, and start operationalizing NHI security in your organization. Machine identities are exploding in scale, complexity, and risk. But with the right strategy, they don’t have to be your blind spot.
.gif)





-p-500.png)
-p-500.png)


